Well that took a while. COVID can really muck things up, but we’re mostly back on track after several months of slow-going.
Encryption passphrase changing
Encryption is great, but it’s only as secure as the encryption key, and the encryption key is only as secure as your passphrase.
Recollectr was released as a minimum viable product (MVP), and that minimum didn’t include allowing users to change their passphrases once set — at least not without jumping through hoops and getting in touch with support. But now that’s all self-serve so you can change your passphrase as often as your heart desires, or as your security needs dictate.
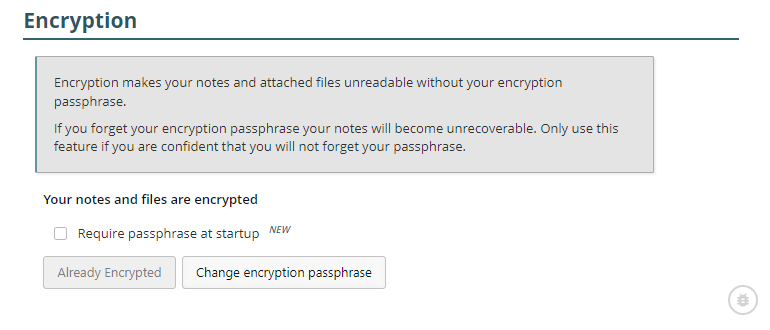
In a related vein, there’s a new mechanism for auto-unlocking your Recollectr installation on startup, doing away with the cumbersome need to enter a password every time you rebooted. This is made possible by using the OS keychain to encrypt your account-level encryption key — so be sure to allow Recollectr access to the keychain if your OS asks you. Auto-unlock is the new default behavior, but for those who want the extra protection, there’s a checkbox to require the passphrase at startup.
Additional security enhancements
Good security isn’t an endpoint; it’s a process. In every release we’re looking at ways to further enhance the security posture of not only the app, but the servers and even our personal workflows to minimize risk in all areas. It’s not a very exciting topic so we don’t talk about it nearly as much as we work on it, but this release brings some notable improvements that are relatively easy to explain (although not so easy to show in pictures.)
In 3.15 and 3.16 we began preparing to enable Electron’s contextIsolation – actually we’d hoped to fully implement it in 3.16 – but doing so turned out to be a bit more difficult than anticipated (and we anticipated it being quite the pain!) So we’ve spent part of this release cycle fixing the remaining blockers and finally getting it enabled, reducing both the attack surface and the potential impact of attacks. To ELI5, contextIsolation basically makes certain variables read-only so that if an attacker tried to redefine them in a malicious way, they would not be able to do so.
Additionally we have implemented Electron Fuses that improve security.
The most notable two fuses are to disable the use of NODE_OPTIONS (although most of them were already disallowed), and another to force the app to load from the bundled ASAR file, making it harder to trick Recollectr into running maliciously modified files. This isn’t foolproof as an attacker could still unbundle the ASAR file, modify the contents, and repackage it — but if an attacker has that level of access to your machine, you’re already in a very bad place. Even so, in the future we plan to prevent that possibility as well. As mentioned above, security is a process.
And a quick honorable mention, macOS builds are now notarized with Apple.
A new way to export your notes
For years we’ve been planning to add the option to export to an RXPT, a Recollectr Export file.
While Recollectr has supported bulk exports for years, it’s always been to export the data to some unencrypted form, like Markdown, HTML, or plain old text. The new RXPT format provides a bulk export option that can maintain the encryption that protects your private data, while still being readable with the help of Recollectr. This makes it a great format for backups and archives, especially for sensitive data.
You’ll find the new RXPT option under the Export Notes section of the Settings screen.
Implementing the new RXPT option means Recollectr now supports command line arguments… well, one argument at least… In the future we’ll add more to enable things like programmatically creating exports, but for now the only argument is --useRXPT=[path], which will open the RXPT in read-only mode and display the data inside Recollectr, where it can be explored or exported.
Styling optimizations
Style rules are generally considered to have a trivial effect on performance, but that notion is rather mistaken, especially in the context of a text editor. Whenever an element is added or moved, and in other cases as well, the browser engine needs to recalculate the sizes and positions for all the other elements on the page in what is known as a reflow.
Two of the main factors in how long a reflow takes are the number of elements on the page and the amount/complexity of style rules the engine needs to process.
We’ve already done about as much as we can to reduce the number of elements on the page in previous releases, so we turned our attention to the other factor, the number of style rules, and their complexity. These changes should be especially noticeable when working with longer documents as the effect of reflows is more significant with more elements on the page.
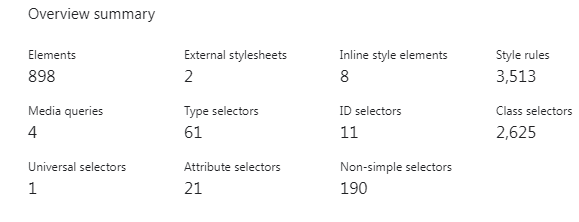
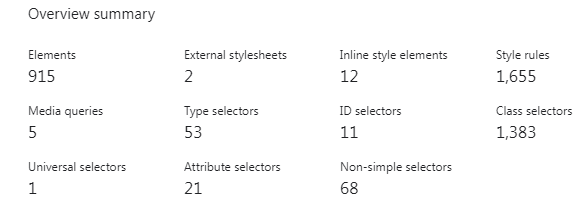
Below you can see a quick overview of the styles when viewing the Quickstart Guide note. We’ve reduced the number of style rules by 53%, and the number of non-simple selectors by 64%.
Some other notable tweaks & fixes
There are a lot more changes in this release; here are just five we’ve selected to highlight.
- Improved CSS syntax highlighting
- Enabled the Hermes JavaScript engine for Recollectr Mobile for improved performance
- Fixed link auto-detection only supported TLDs of 6 characters or less
- Fixed inconsistent hexcode color detection within inline code
- Fixed CORS issue that prevented downloading images from pasted HTML
Stay tuned for more; we’re hoping to launch a feature request tracker shortly!
Check out the Recollectr 3.17 changelog for a full list of changes